IS-IS Lab 18 Authentication
Previous Next
Download Lab: VIRL | EVE-NG | GNS3
Image requirements:
Cisco IOSv (vios-adventerprisek9-m.vmdk.SPA.156-2.T)
Introduction:
This lab all about securing IS-IS protocol, there are three methods that can be used to protect IS-IS: enable authentication between directly connected neighbors, authenticate area, and deploy domain-wide authentication. All these methods can be configured as clear-text or MD5. Also, there are two ways to enable IS-IS authentication, the old one, where a password is directly configured under the IS-IS configuration mode which only works with plain-text and the new one when key-chain is used. All mentioned aspects of IS-IS security will be implemented in this lab.
Nodes Access:
Enable: cisco
Username: cisco
Password: cisco
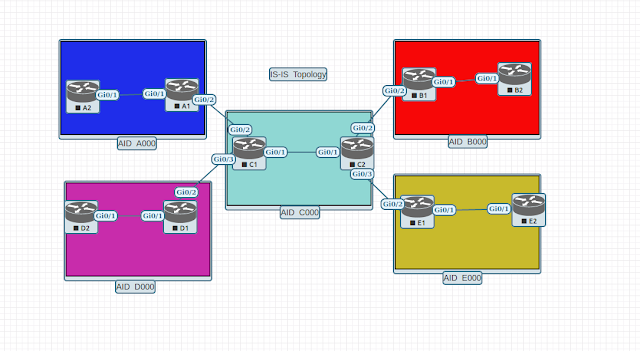
Topology:
Lab tasks:
1. Configure clear-text authentication between routers A1 and A2 using old-style on the A1 side and key-chain on the A2 side of the link.
2. Configure MD5 authentication between routers B1 and B2, using key-chain for both routers.
3. Configure clear-text area authentication between routers D1 and D2.
4. Configure MD5 area authentication between routers E1 and E2.
5. Configure domain-wide clear-text authentication between core routers and their L1/L2 neighbors.
6. Upgrade domain-wide clear-text authentication to MD5 authentication.
7. Configure MD5 L2 adjacency authentication between core routers and their L1/L2 neighbors.
8. Troubleshooting area authentication.
Lab procedure:
Task1: clear-text authentication between neighbors.
Step1: Configuring old type text authentication on router A1 under the interface g0/1:
A1(config)#interface g0/1
A1(config-if)#isis password cisco
Step2: Observe with debugging command IS-IS authentication failure:
A1#debug isis authentication information
IS-IS authentication information debugging is on for router process null
A1#
*Dec 28 22:42:57.909: ISIS-AuthInfo: No auth TLV found in received packet
*Dec 28 22:43:07.082: ISIS-AuthInfo: No auth TLV found in received packet
*Dec 28 22:43:07.082: %CLNS-4-AUTH_FAIL: ISIS: LAN IIH authentication failed
A1#
*Dec 28 22:43:17.077: ISIS-AuthInfo: No auth TLV found in received packet
A1#undebug all
All possible debugging has been turned off
A1#
Step3: Configure key-chain IS-IS with key 1 and the string "cisco" on the router A2:
A2(config)#key chain IS-IS
A2(config-keychain)#key 1
A2(config-keychain-key)#key-string cisco
A2(config-keychain-key)#exit
Step4: Enable IS-IS authentication under G0/1 interface using key-chain on the router A2:
A2(config)#interface g0/1
A2(config-if)#isis authentication mode text
A2(config-if)#isis authentication key-chain IS-IS
Step5: Verify that L1 adjacency is up and save running-config on both routers:
A2#show isis neighbors System Id Type Interface IP Address State Holdtime Circuit Id
A1 L1 Gi0/1 10.0.0.25 UP 22 A2.01
A2#
!A2#copy running-config startup-config
Destination filename [startup-config]?
Building configuration...
[OK]
A2#
Task2: MD5 authentication between neighbors
Step1: IS-IS allows uninterruptedly implement authentication between two peers by temporarily enable authentication in the send-only mode which makes authentication enabled node maintain adjacency with another IS-IS router while it is being configured for the security of IS-IS protocol. Enable authentication send-only mode on router B1 under the g0/1 interface.
B1(config)#interface g0/1
B1(config-if)#isis authentication send-only
Step2: Configure key-chain IS-IS with key 1 and the string "cisco" on the router B1:
B1(config)#key chain IS-IS
B1(config-keychain)#key 1
B1(config-keychain-key)#key-string cisco
B1(config-keychain-key)#exit
Step3: Configure MD5 authentication under G0/1 interface using key-chain on router B1:
B1(config)#interface g0/1
B1(config-if)#isis authentication mode md5
B1(config-if)#isis authentication key-chain IS-IS
Step4: Verify that L1 adjacency with router B2 is still intact and the debug authentication command will not report any failure.
B1#show isis neighbors
System Id Type Interface IP Address State Holdtime Circuit Id
B2 L1 Gi0/1 10.0.0.18 UP 8 B2.01
C2 L2 Gi0/2 10.0.0.22 UP 9 C2.02
B1#debug isis authentication information
IS-IS authentication information debugging is on for router process null
B1#
*Dec 29 00:02:14.889: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:02:24.355: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:02:32.098: ISIS-AuthInfo: IIH no change, use the same hmac value
B1#undebug all
All possible debugging has been turned off
Step5: Configure key-chain IS-IS with key 1 and the string "cisco" on the router B2:
B2(config)#key chain IS-IS
B2(config-keychain)#key 1
B2(config-keychain-key)#key-string cisco
B2(config-keychain-key)#exit
Step6: Configure MD5 authentication under G0/1 interface using key-chain on router B2:
B2(config)#interface g0/1
B2(config-if)#isis authentication mode md5
B2(config-if)#isis authentication key-chain IS-IS
Step7: Remove command authentication send-only from the interface g0/1 on the router B1:
B1(config)#interface g0/1
B1(config-if)#no isis authentication send-only
Step8: Verify that MD5 authentication is working properly between nodes B1 and B2:
B1#debug isis authentication information
IS-IS authentication information debugging is on for router process null
B1#
B1#
*Dec 29 00:16:17.982: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:16:25.809: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:16:35.369: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:16:44.408: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:16:52.186: ISIS-AuthInfo: IIH no change, use the same hmac value
B1#undebug all
All possible debugging has been turned off
Step9: Verify IS-IS L1 adjacency between B1 and B2 and save running-config on both routers.
B1#show isis neighbors
System Id Type Interface IP Address State Holdtime Circuit Id
B2 L1 Gi0/1 10.0.0.18 UP 6 B2.01
C2 L2 Gi0/2 10.0.0.22 UP 9 C2.02
B1#copy running-config startup-config
Destination filename [startup-config]?
Building configuration...
[OK]
B1#
Task3: Clear-text area authentication
Step1: Configure plain-text area authentication under IS-IS router configuration mode on router D1:
D1(config)#router isis
D1(config-router)#area-password cisco
Step2: Configure plain-text area authentication under IS-IS router configuration mode on router D2:
D2(config)#router isis
D2(config-router)#area-password cisco
Note: Remember that area authentication only authenticate LSPs but not adjacencies. If the password on one of the peers is incorrect, neighborship will not go down between IS-IS routers.
Step3: Save running-config.
Task4: MD5 area authentication.
Step1: Configure key-chain IS-IS with key 1 and the string "cisco" on the router E1:
E1(config)#key chain IS-IS
E1(config-keychain)#key 1
E1(config-keychain-key)#key-string cisco
E1(config-keychain-key)#exit
Step2: Enable authentication send-only under router IS-IS configuration mode on the router E1 to prevent connectivity loss during configuration.
E1(config-router)#isis
E1(config-router)#authentication send-only
Step3: Configure under router IS-IS configuration mode area authentication using key-chain on the router E1:
E1(config)#router isis
E1(config-router)#authentication mode md5 level-1
E1(config-router)#authentication key-chain IS-IS level-1
E1(config-router)# exit
Step4: Configure key-chain IS-IS with ke1 and the string "cisco" on the router E2:
E2(config)#key chain IS-IS
E2(config-keychain)#key 1
E2(config-keychain-key)#key-string cisco
E2(config-keychain-key)#exit
Step5: Configure under router IS-IS configuration mode area authentication using key-chain on the router E2:
E2(config)#router isis
E2(config-router)#authentication mode md5 level-1
E2(config-router)#authentication key-chain IS-IS level-1
E2(config-router)# exit
Step6: Remove the authentication send-only command configured in step 2.
E1(config)#router isis
E1(config-router)#no authentication send-only
Step7: Save running-config.
Task5: Domain-wide clear-text authentication
Step1: Configure domain-wide authentication on the router C1:
C1(config)#router isis
C1(config-router)#domain-password cisco
Step2: From the router A2 ping loopback0 IP addresses of C1, B2, D2, E2, it will confirm that connectivity is broken due to IS-IS authentication incomplete configuration:
A2#ping 192.168.0.6
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.6, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
A2#ping 192.168.0.9
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.9, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
A2#ping 192.168.0.7
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.7, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
A2#ping 192.168.0.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.4, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Step3: Configure the same way as in step1 all routers participating in L2 IS-IS topology. (C1, A1, B1, D1, E1).
Step4: Repeat ping again as instructed in step2 to verify that communication can occur.
Task6: MD5 domain-wide authentication
Step1: Configure key-chain IS-IS with key 1 and the string "cisco" on the router C1:
C1(config)#key chain IS-IS
C1(config-keychain)#key 1
C1(config-keychain-key)#key-string cisco
C1(config-keychain-key)#exit
Step2: Remove deprecated old-style password configuration for domain authentication on the router C1:
C1(config)#router isis
C1(config-router)#no domain-password
Step3: Configure MD5 domain-wide authentication on the router C1:
C1(config)#router isis
C1(config-router)#authentication mode md5 level-2
C1(config-router)#authentication key-chain IS-IS level-2
Step4: Repeat steps 1-3 for routers C2, A1, D1.
Step5: Repeat steps 2-3 for router B1 and E1 since key-chain has been configured on those nodes in the previous tasks.
Step6: Save running-config on all affected routers.
Note: Remember that domain-wide authentication like an area authentication only affects LSPs messages.
Task7: MD5 L2 adjacency authentication
Step1: Configure router C1 to authenticate its neighbors using MD5 configuration on its interfaces without breaking L2 adjacencies:
C1(config)#interface range g0/1-3
C1(config-if-range)#isis authentication send-only
C1(config-if-range)#isis authentication mode md5 level-2
C1(config-if-range)#isis authentication key-chain IS-IS level-2
Step2: Configure router C2 to authenticate its neighbors using MD5 configuration on its interfaces without breaking L2 adjacencies:
C2(config)#interface range g0/1-3
C2(config-if-range)#isis authentication send-only
C2(config-if-range)#isis authentication mode md5 level-2
C2(config-if-range)#isis authentication key-chain IS-IS level-2
Step3: Configure all L1/L2 routers to have MD5 authentication enabled with core routers C1 and C2.
A1(config)#interface g0/2
A1(config-if)#isis authentication mode md5 level-2
A1(config-if)#isis authentication key-chain IS-IS level-2
B1(config)#interface g0/2
B1(config-if)#isis authentication mode md5 level-2
B1(config-if)#isis authentication key-chain IS-IS level-2
D1(config)#interface g0/2
D1(config-if)#isis authentication mode md5 level-2
D1(config-if)#isis authentication key-chain IS-IS level-2
E1(config)#interface g0/2
E1(config-if)#isis authentication mode md5 level-2
E1(config-if)#isis authentication key-chain IS-IS level-2
Step4: Remove authentication send-only command from router C1:
C1(config)#interface range g0/1-3
C1(config-if-range)#no isis authentication send-only
Step5: Remove authentication send-only command from router C2:
C2(config)#interface range g0/1-3
C2(config-if-range)#no isis authentication send-only
Step6: Verify IS-IS neighborships, execute this show command multiple times, pay attention to the "holdtime" column if counters do not get refreshed it indicates that authentication configured incorrectly between neighbors.
C1#show isis neighbors
System Id Type Interface IP Address State Holdtime Circuit Id
A1 L2 Gi0/2 10.0.0.9 UP 28 C1.02
C2 L2 Gi0/1 10.0.0.34 UP 22 C1.01
D1 L2 Gi0/3 10.0.0.6 UP 8 D1.02
C1#
Step7: Save running-config on all affected routers.
Task8: Troubleshooting area authentication. This part of the lab will show how to troubleshoot connectivity issues due to the area or domain-wide authentication improper configuration.
Scenario: Router A2 is unable to access loopback0's IP address of router D2.
Router D2 has been configured with an incorrect area authentication.
Step1: Modify password to "cisco1" on the router D2 for IS-IS area authentication to simulate failure.
D2(config)#router isis
D2(config-router)#area-password cisco1
D2(config-router)#end
Step2: Next, verify that router A2 is unable to ping loopback0's IP address of router D2:
A2#ping 192.168.0.9
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.9, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
A2#
Step3: Troubleshooting procedure, step2 identifies that there is a problem with connectivity, router A2 has no connection to router D2. Diagram obviously outlines that router D2 is in IS-IS area D000 and that router D1 is the border router, it would be a nice idea to check if there is connectivity to router D1:
A2#ping 192.168.0.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/5/6 ms
A2#
Successful ping to loopback0's IP address of router D1 gives the clue that the problem might be local to the IS-IS area D000.
Step4: Jumping to the CLI of D1, verify if the router this able to ping D2's loopback0's IP address:
D1#ping 192.168.0.9
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.9, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
D1#
While doing this part of the lab, disregard the LPS authentication failure messages for the sake of troubleshooting learning.
Step5: Verify if router D1 able to communicate with router D2 over the link they share to establish an L1 adjacency. Simply see if there is neighborship is up between two nodes.
D1#show isis neighbors
System Id Type Interface IP Address State Holdtime Circuit Id
C1 L2 Gi0/2 10.0.0.5 UP 27 D1.02
D2 L1 Gi0/1 10.0.0.30 UP 24 D1.01
D2 is up, but D1 still unable to ping loopback0' IP address.
Step6: Since neighborship with D2 is active, proceed to verify database D1 receives from D2:
D1#show isis database level-1
IS-IS Level-1 Link State Database:
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
D1.00-00 * 0x0000001F 0x3717 989/* 1/0/0
D1.01-00 * 0x0000001A 0xB4ED 582/* 0/0/0
There is a missing LSP of D2 in D1's database.
Step7: The next step will be checking the running configuration for the IS-IS router portion on both routers to spot if there is a difference between the two configs.
D1#show running-config | section router isis
ip router isis
ip router isis
ip router isis
router isis
net 49.d000.0000.0000.00d1.00
area-password cisco
authentication mode md5 level-2
authentication key-chain IS-IS level-2
log-adjacency-changes
!
router isis
net 49.d000.0000.0000.00d2.00
is-type level-1
area-password cisco1
The output shows that there is a difference in the area-password line.
Step8: Fixing the issue, according to documentation the password should be "cisco" and not "cisco1", that is why router D2's password will be changed.
D2(config)#router isis
D2(config-router)#area-password cisco
D2(config-router)#end
Step9: Confirm that router D1 now has LSP of router D2 in its database:
D1#show isis database level-1
IS-IS Level-1 Link State Database:
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
D1.00-00 * 0x00000020 0x3518 809/* 1/0/0
D1.01-00 * 0x0000001C 0xB0EF 1025/* 0/0/0
D2.00-00 0x00000021 0xB592 1034/1199 0/0/0
Indeed, D2 LSP is present in the database. Let's check what is inside of the LSP:
D1#show isis database detail D2.00-00
IS-IS Level-1 LSP D2.00-00
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
D2.00-00 0x00000021 0xB592 943/1199 0/0/0
Auth: Length: 6
Area Address: 49.d000
NLPID: 0xCC
Hostname: D2
Metric: 10 IS D1.01
IP Address: 192.168.0.9
Metric: 10 IP 10.0.0.28 255.255.255.252
Metric: 10 IP 192.168.0.9 255.255.255.255
Prefix for loopback0' interface is included, meaning that D1 will advertise it into L2 topology, verifying D1's L2 LSP will prove that A2 might be able to ping D2's loopback IP address:
D1#show isis database detail D1.00-00 level-2
IS-IS Level-2 LSP D1.00-00
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
D1.00-00 * 0x00000024 0xAFBD 682/* 0/0/0
Auth: Length: 17
Area Address: 49.d000
NLPID: 0xCC
Hostname: D1
Metric: 10 IS D1.02
IP Address: 192.168.0.3
Metric: 10 IP 10.0.0.4 255.255.255.252
Metric: 10 IP 10.0.0.28 255.255.255.252
Metric: 10 IP 192.168.0.3 255.255.255.255
Metric: 20 IP 192.168.0.9 255.255.255.255
Prefix with metric 20 is D2's IP address of loopback0.
Step10: Lastly let's see if router A2 able to ping 192.168.0.9.
A2#ping 192.168.0.9
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.9, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 3/5/7 ms
A2#
Troubleshooting was successful.
Download Lab: VIRL | EVE-NG | GNS3
Image requirements:
Cisco IOSv (vios-adventerprisek9-m.vmdk.SPA.156-2.T)
Introduction:
This lab all about securing IS-IS protocol, there are three methods that can be used to protect IS-IS: enable authentication between directly connected neighbors, authenticate area, and deploy domain-wide authentication. All these methods can be configured as clear-text or MD5. Also, there are two ways to enable IS-IS authentication, the old one, where a password is directly configured under the IS-IS configuration mode which only works with plain-text and the new one when key-chain is used. All mentioned aspects of IS-IS security will be implemented in this lab.
Nodes Access:
Enable: cisco
Username: cisco
Password: cisco
Topology:
Lab tasks:
1. Configure clear-text authentication between routers A1 and A2 using old-style on the A1 side and key-chain on the A2 side of the link.
2. Configure MD5 authentication between routers B1 and B2, using key-chain for both routers.
3. Configure clear-text area authentication between routers D1 and D2.
4. Configure MD5 area authentication between routers E1 and E2.
5. Configure domain-wide clear-text authentication between core routers and their L1/L2 neighbors.
6. Upgrade domain-wide clear-text authentication to MD5 authentication.
7. Configure MD5 L2 adjacency authentication between core routers and their L1/L2 neighbors.
8. Troubleshooting area authentication.
Lab procedure:
Task1: clear-text authentication between neighbors.
Step1: Configuring old type text authentication on router A1 under the interface g0/1:
A1(config)#interface g0/1
A1(config-if)#isis password cisco
Step2: Observe with debugging command IS-IS authentication failure:
A1#debug isis authentication information
IS-IS authentication information debugging is on for router process null
A1#
*Dec 28 22:42:57.909: ISIS-AuthInfo: No auth TLV found in received packet
*Dec 28 22:43:07.082: ISIS-AuthInfo: No auth TLV found in received packet
*Dec 28 22:43:07.082: %CLNS-4-AUTH_FAIL: ISIS: LAN IIH authentication failed
A1#
*Dec 28 22:43:17.077: ISIS-AuthInfo: No auth TLV found in received packet
A1#undebug all
All possible debugging has been turned off
A1#
Step3: Configure key-chain IS-IS with key 1 and the string "cisco" on the router A2:
A2(config)#key chain IS-IS
A2(config-keychain)#key 1
A2(config-keychain-key)#key-string cisco
A2(config-keychain-key)#exit
Step4: Enable IS-IS authentication under G0/1 interface using key-chain on the router A2:
A2(config)#interface g0/1
A2(config-if)#isis authentication mode text
A2(config-if)#isis authentication key-chain IS-IS
Step5: Verify that L1 adjacency is up and save running-config on both routers:
A2#show isis neighbors System Id Type Interface IP Address State Holdtime Circuit Id
A1 L1 Gi0/1 10.0.0.25 UP 22 A2.01
A2#
!A2#copy running-config startup-config
Destination filename [startup-config]?
Building configuration...
[OK]
A2#
Task2: MD5 authentication between neighbors
Step1: IS-IS allows uninterruptedly implement authentication between two peers by temporarily enable authentication in the send-only mode which makes authentication enabled node maintain adjacency with another IS-IS router while it is being configured for the security of IS-IS protocol. Enable authentication send-only mode on router B1 under the g0/1 interface.
B1(config)#interface g0/1
B1(config-if)#isis authentication send-only
Step2: Configure key-chain IS-IS with key 1 and the string "cisco" on the router B1:
B1(config)#key chain IS-IS
B1(config-keychain)#key 1
B1(config-keychain-key)#key-string cisco
B1(config-keychain-key)#exit
Step3: Configure MD5 authentication under G0/1 interface using key-chain on router B1:
B1(config)#interface g0/1
B1(config-if)#isis authentication mode md5
B1(config-if)#isis authentication key-chain IS-IS
Step4: Verify that L1 adjacency with router B2 is still intact and the debug authentication command will not report any failure.
B1#show isis neighbors
System Id Type Interface IP Address State Holdtime Circuit Id
B2 L1 Gi0/1 10.0.0.18 UP 8 B2.01
C2 L2 Gi0/2 10.0.0.22 UP 9 C2.02
B1#debug isis authentication information
IS-IS authentication information debugging is on for router process null
B1#
*Dec 29 00:02:14.889: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:02:24.355: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:02:32.098: ISIS-AuthInfo: IIH no change, use the same hmac value
B1#undebug all
All possible debugging has been turned off
Step5: Configure key-chain IS-IS with key 1 and the string "cisco" on the router B2:
B2(config)#key chain IS-IS
B2(config-keychain)#key 1
B2(config-keychain-key)#key-string cisco
B2(config-keychain-key)#exit
Step6: Configure MD5 authentication under G0/1 interface using key-chain on router B2:
B2(config)#interface g0/1
B2(config-if)#isis authentication mode md5
B2(config-if)#isis authentication key-chain IS-IS
Step7: Remove command authentication send-only from the interface g0/1 on the router B1:
B1(config)#interface g0/1
B1(config-if)#no isis authentication send-only
Step8: Verify that MD5 authentication is working properly between nodes B1 and B2:
B1#debug isis authentication information
IS-IS authentication information debugging is on for router process null
B1#
B1#
*Dec 29 00:16:17.982: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:16:25.809: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:16:35.369: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:16:44.408: ISIS-AuthInfo: IIH no change, use the same hmac value
*Dec 29 00:16:52.186: ISIS-AuthInfo: IIH no change, use the same hmac value
B1#undebug all
All possible debugging has been turned off
Step9: Verify IS-IS L1 adjacency between B1 and B2 and save running-config on both routers.
B1#show isis neighbors
System Id Type Interface IP Address State Holdtime Circuit Id
B2 L1 Gi0/1 10.0.0.18 UP 6 B2.01
C2 L2 Gi0/2 10.0.0.22 UP 9 C2.02
B1#copy running-config startup-config
Destination filename [startup-config]?
Building configuration...
[OK]
B1#
Task3: Clear-text area authentication
Step1: Configure plain-text area authentication under IS-IS router configuration mode on router D1:
D1(config)#router isis
D1(config-router)#area-password cisco
Step2: Configure plain-text area authentication under IS-IS router configuration mode on router D2:
D2(config)#router isis
D2(config-router)#area-password cisco
Note: Remember that area authentication only authenticate LSPs but not adjacencies. If the password on one of the peers is incorrect, neighborship will not go down between IS-IS routers.
Step3: Save running-config.
Task4: MD5 area authentication.
Step1: Configure key-chain IS-IS with key 1 and the string "cisco" on the router E1:
E1(config)#key chain IS-IS
E1(config-keychain)#key 1
E1(config-keychain-key)#key-string cisco
E1(config-keychain-key)#exit
Step2: Enable authentication send-only under router IS-IS configuration mode on the router E1 to prevent connectivity loss during configuration.
E1(config-router)#isis
E1(config-router)#authentication send-only
Step3: Configure under router IS-IS configuration mode area authentication using key-chain on the router E1:
E1(config)#router isis
E1(config-router)#authentication mode md5 level-1
E1(config-router)#authentication key-chain IS-IS level-1
E1(config-router)# exit
Step4: Configure key-chain IS-IS with ke1 and the string "cisco" on the router E2:
E2(config)#key chain IS-IS
E2(config-keychain)#key 1
E2(config-keychain-key)#key-string cisco
E2(config-keychain-key)#exit
Step5: Configure under router IS-IS configuration mode area authentication using key-chain on the router E2:
E2(config)#router isis
E2(config-router)#authentication mode md5 level-1
E2(config-router)#authentication key-chain IS-IS level-1
E2(config-router)# exit
Step6: Remove the authentication send-only command configured in step 2.
E1(config)#router isis
E1(config-router)#no authentication send-only
Step7: Save running-config.
Task5: Domain-wide clear-text authentication
Step1: Configure domain-wide authentication on the router C1:
C1(config)#router isis
C1(config-router)#domain-password cisco
Step2: From the router A2 ping loopback0 IP addresses of C1, B2, D2, E2, it will confirm that connectivity is broken due to IS-IS authentication incomplete configuration:
A2#ping 192.168.0.6
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.6, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
A2#ping 192.168.0.9
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.9, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
A2#ping 192.168.0.7
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.7, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
A2#ping 192.168.0.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.4, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Step3: Configure the same way as in step1 all routers participating in L2 IS-IS topology. (C1, A1, B1, D1, E1).
Step4: Repeat ping again as instructed in step2 to verify that communication can occur.
Task6: MD5 domain-wide authentication
Step1: Configure key-chain IS-IS with key 1 and the string "cisco" on the router C1:
C1(config)#key chain IS-IS
C1(config-keychain)#key 1
C1(config-keychain-key)#key-string cisco
C1(config-keychain-key)#exit
Step2: Remove deprecated old-style password configuration for domain authentication on the router C1:
C1(config)#router isis
C1(config-router)#no domain-password
Step3: Configure MD5 domain-wide authentication on the router C1:
C1(config)#router isis
C1(config-router)#authentication mode md5 level-2
C1(config-router)#authentication key-chain IS-IS level-2
Step4: Repeat steps 1-3 for routers C2, A1, D1.
Step5: Repeat steps 2-3 for router B1 and E1 since key-chain has been configured on those nodes in the previous tasks.
Step6: Save running-config on all affected routers.
Note: Remember that domain-wide authentication like an area authentication only affects LSPs messages.
Task7: MD5 L2 adjacency authentication
Step1: Configure router C1 to authenticate its neighbors using MD5 configuration on its interfaces without breaking L2 adjacencies:
C1(config)#interface range g0/1-3
C1(config-if-range)#isis authentication send-only
C1(config-if-range)#isis authentication mode md5 level-2
C1(config-if-range)#isis authentication key-chain IS-IS level-2
Step2: Configure router C2 to authenticate its neighbors using MD5 configuration on its interfaces without breaking L2 adjacencies:
C2(config)#interface range g0/1-3
C2(config-if-range)#isis authentication send-only
C2(config-if-range)#isis authentication mode md5 level-2
C2(config-if-range)#isis authentication key-chain IS-IS level-2
Step3: Configure all L1/L2 routers to have MD5 authentication enabled with core routers C1 and C2.
A1(config)#interface g0/2
A1(config-if)#isis authentication mode md5 level-2
A1(config-if)#isis authentication key-chain IS-IS level-2
B1(config)#interface g0/2
B1(config-if)#isis authentication mode md5 level-2
B1(config-if)#isis authentication key-chain IS-IS level-2
D1(config)#interface g0/2
D1(config-if)#isis authentication mode md5 level-2
D1(config-if)#isis authentication key-chain IS-IS level-2
E1(config)#interface g0/2
E1(config-if)#isis authentication mode md5 level-2
E1(config-if)#isis authentication key-chain IS-IS level-2
Step4: Remove authentication send-only command from router C1:
C1(config)#interface range g0/1-3
C1(config-if-range)#no isis authentication send-only
Step5: Remove authentication send-only command from router C2:
C2(config)#interface range g0/1-3
C2(config-if-range)#no isis authentication send-only
Step6: Verify IS-IS neighborships, execute this show command multiple times, pay attention to the "holdtime" column if counters do not get refreshed it indicates that authentication configured incorrectly between neighbors.
C1#show isis neighbors
System Id Type Interface IP Address State Holdtime Circuit Id
A1 L2 Gi0/2 10.0.0.9 UP 28 C1.02
C2 L2 Gi0/1 10.0.0.34 UP 22 C1.01
D1 L2 Gi0/3 10.0.0.6 UP 8 D1.02
C1#
Step7: Save running-config on all affected routers.
Task8: Troubleshooting area authentication. This part of the lab will show how to troubleshoot connectivity issues due to the area or domain-wide authentication improper configuration.
Scenario: Router A2 is unable to access loopback0's IP address of router D2.
Router D2 has been configured with an incorrect area authentication.
Step1: Modify password to "cisco1" on the router D2 for IS-IS area authentication to simulate failure.
D2(config)#router isis
D2(config-router)#area-password cisco1
D2(config-router)#end
Step2: Next, verify that router A2 is unable to ping loopback0's IP address of router D2:
A2#ping 192.168.0.9
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.9, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
A2#
Step3: Troubleshooting procedure, step2 identifies that there is a problem with connectivity, router A2 has no connection to router D2. Diagram obviously outlines that router D2 is in IS-IS area D000 and that router D1 is the border router, it would be a nice idea to check if there is connectivity to router D1:
A2#ping 192.168.0.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/5/6 ms
A2#
Successful ping to loopback0's IP address of router D1 gives the clue that the problem might be local to the IS-IS area D000.
Step4: Jumping to the CLI of D1, verify if the router this able to ping D2's loopback0's IP address:
D1#ping 192.168.0.9
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.9, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
D1#
While doing this part of the lab, disregard the LPS authentication failure messages for the sake of troubleshooting learning.
Step5: Verify if router D1 able to communicate with router D2 over the link they share to establish an L1 adjacency. Simply see if there is neighborship is up between two nodes.
D1#show isis neighbors
System Id Type Interface IP Address State Holdtime Circuit Id
C1 L2 Gi0/2 10.0.0.5 UP 27 D1.02
D2 L1 Gi0/1 10.0.0.30 UP 24 D1.01
D2 is up, but D1 still unable to ping loopback0' IP address.
Step6: Since neighborship with D2 is active, proceed to verify database D1 receives from D2:
D1#show isis database level-1
IS-IS Level-1 Link State Database:
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
D1.00-00 * 0x0000001F 0x3717 989/* 1/0/0
D1.01-00 * 0x0000001A 0xB4ED 582/* 0/0/0
There is a missing LSP of D2 in D1's database.
Step7: The next step will be checking the running configuration for the IS-IS router portion on both routers to spot if there is a difference between the two configs.
D1#show running-config | section router isis
ip router isis
ip router isis
ip router isis
router isis
net 49.d000.0000.0000.00d1.00
area-password cisco
authentication mode md5 level-2
authentication key-chain IS-IS level-2
log-adjacency-changes
!
router isis
net 49.d000.0000.0000.00d2.00
is-type level-1
area-password cisco1
The output shows that there is a difference in the area-password line.
Step8: Fixing the issue, according to documentation the password should be "cisco" and not "cisco1", that is why router D2's password will be changed.
D2(config)#router isis
D2(config-router)#area-password cisco
D2(config-router)#end
Step9: Confirm that router D1 now has LSP of router D2 in its database:
D1#show isis database level-1
IS-IS Level-1 Link State Database:
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
D1.00-00 * 0x00000020 0x3518 809/* 1/0/0
D1.01-00 * 0x0000001C 0xB0EF 1025/* 0/0/0
D2.00-00 0x00000021 0xB592 1034/1199 0/0/0
Indeed, D2 LSP is present in the database. Let's check what is inside of the LSP:
D1#show isis database detail D2.00-00
IS-IS Level-1 LSP D2.00-00
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
D2.00-00 0x00000021 0xB592 943/1199 0/0/0
Auth: Length: 6
Area Address: 49.d000
NLPID: 0xCC
Hostname: D2
Metric: 10 IS D1.01
IP Address: 192.168.0.9
Metric: 10 IP 10.0.0.28 255.255.255.252
Metric: 10 IP 192.168.0.9 255.255.255.255
Prefix for loopback0' interface is included, meaning that D1 will advertise it into L2 topology, verifying D1's L2 LSP will prove that A2 might be able to ping D2's loopback IP address:
D1#show isis database detail D1.00-00 level-2
IS-IS Level-2 LSP D1.00-00
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
D1.00-00 * 0x00000024 0xAFBD 682/* 0/0/0
Auth: Length: 17
Area Address: 49.d000
NLPID: 0xCC
Hostname: D1
Metric: 10 IS D1.02
IP Address: 192.168.0.3
Metric: 10 IP 10.0.0.4 255.255.255.252
Metric: 10 IP 10.0.0.28 255.255.255.252
Metric: 10 IP 192.168.0.3 255.255.255.255
Metric: 20 IP 192.168.0.9 255.255.255.255
Prefix with metric 20 is D2's IP address of loopback0.
Step10: Lastly let's see if router A2 able to ping 192.168.0.9.
A2#ping 192.168.0.9
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.9, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 3/5/7 ms
A2#
Troubleshooting was successful.

Comments
Post a Comment