IS-IS Lab 24 Route Leaking
Previous Next
Download Lab: VIRL | EVE-NG | GNS3
Image requirements:
Cisco IOSv (vios-adventerprisek9-m.vmdk.SPA.156-2.T)
Introduction:
By default IS-IS L1 area is like "Totally stub area" in the OSPF, meaning that L1/L2 node will not advertise any routes learned from other parts of IS-IS domain into L1 area, instead of when L1/L2 router communicates with the L1 only node it sends its link-state database update with attach bit set to 1 when L1 router receives this type of update it installs a default route into its routing table pointing to the nearest L1/L2 router and through this quad zero route L1 only router able to reach the rest of IS-IS topology. This lab will introduce the route leaking technique which allows bending the default behavior and propagates some of the subnets from the L2 area into the L1 area by the mean of redistribution, this way if there is a suboptimal path to the specific destination due to the default route, leaking approach of the single subnet into the L1 area will eliminate the suboptimal behavior. Even though the topology which is being used in this lab has a singe L1/L2 router per L1 area and there is no possibility for the suboptimal pathing still this topology is good to perform route leaking for sake of the learning experience.
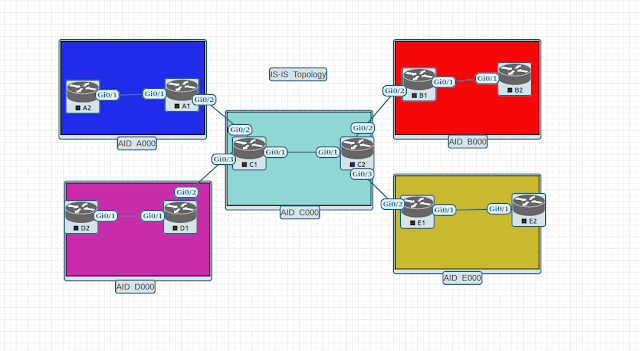
Topology:
Scenario:
Router A1 is the L1/L2 node for the AID A000 will leak the route of the loopback0 interface of router D2 for both IPv4 and IPV6 routed protocols, while identifying the IPV4 route with the use of the access control list and IPv6 prefix by means of prefix-list. For the area B000, the L1/L2 router B1 will be leaking the IPv4 route of router A2's loopback0's IP address and for the IPv6 prefix, this node will advertise prefix of router E2's loopback0's IPv6 address. Both IPv4 and IPv6 route leaking prefixes will be identified by means of prefix-list.
Lab tasks:
1. On the router A1, configure ACL to identify the IPv4 address of D2's loopback0 interface.
2. On the router A1, configure the IPv6 prefix-list to identify the IPv6 address of D2's loopback0 interface.
3. Under the IS-IS global router mode with the use of redistribution command, leak the route identified by the ACL in task 1.
4. Next, enter the configuration mode for IPv6 IS-IS and redistribute prefix identified in task 2 by the IPv6 prefix-list.
5. Display the running-config partially to see the output for the router isis part to determine the proper configuration of route leaking.
6. Verify that a detailed IS-IS database for A1 router on the router A2 has in it IPv4 and IPv6 prefixes for leaked routes.
7. Verify the IPv4 and IPv6 routing tables on the router A2 for the presence of leaked routes. Save configurations on the router A1.
8. Configure the IPv4 prefix-list to identify the IPv4 route of A2's loopback0 interface. Perform this on the router B1.
9. Configure the IPv6 prefix-list to identify the IPv6 route of E2's loopback0 interface. Perform this on the router B1.
10. Configure route leaking for IPv4 first then proceed to IPv6. Perform this on the router B1.
11. Verify that the route leaking configuration was performed properly by checking the running-config on the router B1.
12. On the router, B2 verify that B1 propagates the IPv4 and IPv6 leaked routes by checking both the IS-IS database and routing table.
Lab procedure:
Step1: Configure ACL to match IPv4 address of router D2's loopback0 interface:
!
A1(config)#ip access-list extended 100
A1(config-ext-nacl)#permit ip 192.168.0.9 0.0.0.0 any
A1(config-ext-nacl)#end
!
A1#show ip access-lists Extended IP access list D2-loopback-ipv4
10 permit ip host 192.168.0.9 any
A1#
Step2: Configure prefix-list to match IPv6 prefix of router D2's loopback0 interface then match it under the route-map configuration mode:
A1(config)#ipv6 prefix-list D2-loopback-ipv6 permit 2001:db8:b:0:1::9/128
!
A1#show ipv6 prefix-list ipv6 prefix-list D2-loopback-ipv6: 1 entries
seq 5 permit 2001:DB8:B:0:1::9/128
!
A1(config)#route-map ROUTE_LEAK permit 10
A1(config-route-map)# match ipv6 address prefix-list D2-loopback-ipv6
Step3: Configure route leaking under IS-IS router mode:
!
A1(config)#router isis
A1(config-router)#redistribute isis ip level-2 into level-1 distribute-list 100
Step4: Access IS-IS IPv6 address-family then redistribute L2 IPv6 prefix into L1 area with the help of route-map:
!
A1(config)#router isis
A1(config-router)#address-family ipv6
A1(config-router-af)#redistribute isis level-2 into level-1 route-map ROUTE_LEAK
A1(config-router-af)#end
A1#
Step5: Verify running-config for proper configuration of route leaking:
!
A1#show running-config | section router isisrouter isis
net 49.a000.0000.0000.00a1.00
redistribute isis ip level-2 into level-1 distribute-list 100
!
address-family ipv6
redistribute isis level-2 into level-1 route-map ROUTE_LEAK
exit-address-family
Step6: Check detailed IS-IS database on router A2 to see if leaked prefixes have been redistributed:
!
A2#show isis database detail A1.00-00IS-IS Level-1 LSP A1.00-00
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
A1.00-00 0x00000017 0xD2AD 689/1199 1/0/0
Area Address: 49.a000
NLPID: 0xCC 0x8E
Hostname: A1
Metric: 10 IS A2.01
IP Address: 192.168.0.2
Metric: 10 IP 10.0.0.24 255.255.255.252
Metric: 10 IP 192.168.0.2 255.255.255.255
Metric: 40 IP-Interarea 192.168.0.9 255.255.255.255
IPv6 Address: 2001:DB8:B:0:1::2
Metric: 10 IPv6 2001:DB8:B:0:1::2/128
Metric: 10 IPv6 2001:DB8:A:0:1:1:0:18/126
Metric: 40 IPv6-Interarea 2001:DB8:B:0:1::9/128
The output confirms that both IPv4 and IPv6 routes successfully have been redistributed.
Step7: Verify routing table for both IPv4 and IPv6 routed protocol to see if leaked prefixes have been installed:
!
A2#show ip route isis
Gateway of last resort is 10.0.0.25 to network 0.0.0.0
i*L1 0.0.0.0/0 [115/10] via 10.0.0.25, 04:15:38, GigabitEthernet0/1
192.168.0.0/32 is subnetted, 3 subnets
i L1 192.168.0.2 [115/20] via 10.0.0.25, 00:01:04, GigabitEthernet0/1
i ia 192.168.0.9 [115/50] via 10.0.0.25, 00:01:04, GigabitEthernet0/1
A2# show ipv6 route isis
IPv6 Routing Table - default - 7 entries
I1 ::/0 [115/10]
via FE80::F816:3EFF:FE39:9795, GigabitEthernet0/1
I1 2001:DB8:B:0:1::2/128 [115/20]
via FE80::F816:3EFF:FE39:9795, GigabitEthernet0/1
IA 2001:DB8:B:0:1::9/128 [115/50]
via FE80::F816:3EFF:FE39:9795, GigabitEthernet0/1
Both outputs verify that routes that have been identified to be redistributed from the L2 areas into the L1 area have been installed into routing tables of router A2.
Step8: On router B1, configure IPv4 prefix-list to match the IP address of router A2's loopback0 interface, then configure route-map to match this prefix-list:
!
B1(config)#ip prefix-list A2-loopback-ipv4 permit 192.168.0.10/32
!
B1(config)#route-map ROUTE_LEAK_IPV4 permit 10
B1(config-route-map)#match ip address prefix-list A2-loopback-ipv4
B1(config-route-map)# end
Step9: On router B1, configure IPv6 prefix-list to match the IPv6 address of router E2's loopback0 interface, then configure route-map to match this prefix-list:
!
B1(config)#ipv6 prefix-list E2-loopback-ipv6 permit 2001:db8:b:0:1::b/128
!
B1(config)#route-map ROUTE_LEAK_IPV6 permit 10
B1(config-route-map)#match ipv6 address prefix-list E2-loopback-ipv6
B1(config-route-map)#end
Step10: Redistribute both IPv4 and IPv6 prefixes identified in previous steps 8 and 9:
!
B1(config)#router isis
B1(config-router)#redistribute isis ip level-2 into level-1
route-map ROUTE_LEAK_IPV4
!
B1(config-router)#address-family ipv6
B1(config-router-af)#redistribute isis level-2 into level-1 route-map ROUTE_LEAK_IPV6
B1(config-router-af)#
Step11: Verify that the route leaking configuration was performed properly by checking the running-config on the router B1:
B1#show running-config | section router isisrouter isis
net 49.b000.0000.0000.00b1.00
redistribute isis ip level-2 into level-1 route-map ROUTE_LEAK_IPV4
!
address-family ipv6
redistribute isis level-2 into level-1 route-map ROUTE_LEAK_IPV6
exit-address-family
Step12. On the router, B2 verify that B1 propagates the IPv4 and IPv6 leaked routes by checking both the IS-IS database and routing table:
B2#show isis database detail B1.00-00
IS-IS Level-1 LSP B1.00-00
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
B1.00-00 0x0000001B 0xCC80 838/1199 1/0/0
Area Address: 49.b000
NLPID: 0xCC 0x8E
Hostname: B1
Metric: 10 IS B1.01
IP Address: 192.168.0.1
Metric: 10 IP 10.0.0.16 255.255.255.252
Metric: 10 IP 192.168.0.1 255.255.255.255
Metric: 50 IP-Interarea 192.168.0.10 255.255.255.255
IPv6 Address: 2001:DB8:B:0:1::4
Metric: 10 IPv6 2001:DB8:B:0:1::4/128
Metric: 10 IPv6 2001:DB8:A:0:1:1:0:10/126
Metric: 40 IPv6-Interarea 2001:DB8:B:0:1::B/128
The output confirms that both the IPv4 route of router A2 and IPv6 prefix of router E2 are in the IS-IS database of router B2.
B2#show ip route isis
Gateway of last resort is 10.0.0.17 to network 0.0.0.0
i*L1 0.0.0.0/0 [115/10] via 10.0.0.17, 04:48:12, GigabitEthernet0/1
192.168.0.0/32 is subnetted, 3 subnets
i L1 192.168.0.1 [115/20] via 10.0.0.17, 00:03:51, GigabitEthernet0/1
i ia 192.168.0.10 [115/60] via 10.0.0.17, 00:03:51, GigabitEthernet0/1
!
B2#show ipv6 route isis
IPv6 Routing Table - default - 7 entries
I1 ::/0 [115/10]
via FE80::F816:3EFF:FEFB:95F1, GigabitEthernet0/1
I1 2001:DB8:B:0:1::4/128 [115/20]
via FE80::F816:3EFF:FEFB:95F1, GigabitEthernet0/1
IA 2001:DB8:B:0:1::B/128 [115/50]
via FE80::F816:3EFF:FEFB:95F1, GigabitEthernet0/1
B2#
Finally, show commands for both IPv4 and IPv6 routing tables show that more specific routes to reach routers A2 and E2 have been installed.
Download Lab: VIRL | EVE-NG | GNS3
Image requirements:
Cisco IOSv (vios-adventerprisek9-m.vmdk.SPA.156-2.T)
Introduction:
By default IS-IS L1 area is like "Totally stub area" in the OSPF, meaning that L1/L2 node will not advertise any routes learned from other parts of IS-IS domain into L1 area, instead of when L1/L2 router communicates with the L1 only node it sends its link-state database update with attach bit set to 1 when L1 router receives this type of update it installs a default route into its routing table pointing to the nearest L1/L2 router and through this quad zero route L1 only router able to reach the rest of IS-IS topology. This lab will introduce the route leaking technique which allows bending the default behavior and propagates some of the subnets from the L2 area into the L1 area by the mean of redistribution, this way if there is a suboptimal path to the specific destination due to the default route, leaking approach of the single subnet into the L1 area will eliminate the suboptimal behavior. Even though the topology which is being used in this lab has a singe L1/L2 router per L1 area and there is no possibility for the suboptimal pathing still this topology is good to perform route leaking for sake of the learning experience.
Topology:
Scenario:
Router A1 is the L1/L2 node for the AID A000 will leak the route of the loopback0 interface of router D2 for both IPv4 and IPV6 routed protocols, while identifying the IPV4 route with the use of the access control list and IPv6 prefix by means of prefix-list. For the area B000, the L1/L2 router B1 will be leaking the IPv4 route of router A2's loopback0's IP address and for the IPv6 prefix, this node will advertise prefix of router E2's loopback0's IPv6 address. Both IPv4 and IPv6 route leaking prefixes will be identified by means of prefix-list.
Lab tasks:
1. On the router A1, configure ACL to identify the IPv4 address of D2's loopback0 interface.
2. On the router A1, configure the IPv6 prefix-list to identify the IPv6 address of D2's loopback0 interface.
3. Under the IS-IS global router mode with the use of redistribution command, leak the route identified by the ACL in task 1.
4. Next, enter the configuration mode for IPv6 IS-IS and redistribute prefix identified in task 2 by the IPv6 prefix-list.
5. Display the running-config partially to see the output for the router isis part to determine the proper configuration of route leaking.
6. Verify that a detailed IS-IS database for A1 router on the router A2 has in it IPv4 and IPv6 prefixes for leaked routes.
7. Verify the IPv4 and IPv6 routing tables on the router A2 for the presence of leaked routes. Save configurations on the router A1.
8. Configure the IPv4 prefix-list to identify the IPv4 route of A2's loopback0 interface. Perform this on the router B1.
9. Configure the IPv6 prefix-list to identify the IPv6 route of E2's loopback0 interface. Perform this on the router B1.
10. Configure route leaking for IPv4 first then proceed to IPv6. Perform this on the router B1.
11. Verify that the route leaking configuration was performed properly by checking the running-config on the router B1.
12. On the router, B2 verify that B1 propagates the IPv4 and IPv6 leaked routes by checking both the IS-IS database and routing table.
Lab procedure:
Step1: Configure ACL to match IPv4 address of router D2's loopback0 interface:
!
A1(config)#ip access-list extended 100
A1(config-ext-nacl)#permit ip 192.168.0.9 0.0.0.0 any
A1(config-ext-nacl)#end
!
A1#show ip access-lists Extended IP access list D2-loopback-ipv4
10 permit ip host 192.168.0.9 any
A1#
Step2: Configure prefix-list to match IPv6 prefix of router D2's loopback0 interface then match it under the route-map configuration mode:
A1(config)#ipv6 prefix-list D2-loopback-ipv6 permit 2001:db8:b:0:1::9/128
!
A1#show ipv6 prefix-list ipv6 prefix-list D2-loopback-ipv6: 1 entries
seq 5 permit 2001:DB8:B:0:1::9/128
!
A1(config)#route-map ROUTE_LEAK permit 10
A1(config-route-map)# match ipv6 address prefix-list D2-loopback-ipv6
Step3: Configure route leaking under IS-IS router mode:
!
A1(config)#router isis
A1(config-router)#redistribute isis ip level-2 into level-1 distribute-list 100
Step4: Access IS-IS IPv6 address-family then redistribute L2 IPv6 prefix into L1 area with the help of route-map:
!
A1(config)#router isis
A1(config-router)#address-family ipv6
A1(config-router-af)#redistribute isis level-2 into level-1 route-map ROUTE_LEAK
A1(config-router-af)#end
A1#
Step5: Verify running-config for proper configuration of route leaking:
!
A1#show running-config | section router isisrouter isis
net 49.a000.0000.0000.00a1.00
redistribute isis ip level-2 into level-1 distribute-list 100
!
address-family ipv6
redistribute isis level-2 into level-1 route-map ROUTE_LEAK
exit-address-family
Step6: Check detailed IS-IS database on router A2 to see if leaked prefixes have been redistributed:
!
A2#show isis database detail A1.00-00IS-IS Level-1 LSP A1.00-00
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
A1.00-00 0x00000017 0xD2AD 689/1199 1/0/0
Area Address: 49.a000
NLPID: 0xCC 0x8E
Hostname: A1
Metric: 10 IS A2.01
IP Address: 192.168.0.2
Metric: 10 IP 10.0.0.24 255.255.255.252
Metric: 10 IP 192.168.0.2 255.255.255.255
Metric: 40 IP-Interarea 192.168.0.9 255.255.255.255
IPv6 Address: 2001:DB8:B:0:1::2
Metric: 10 IPv6 2001:DB8:B:0:1::2/128
Metric: 10 IPv6 2001:DB8:A:0:1:1:0:18/126
Metric: 40 IPv6-Interarea 2001:DB8:B:0:1::9/128
The output confirms that both IPv4 and IPv6 routes successfully have been redistributed.
Step7: Verify routing table for both IPv4 and IPv6 routed protocol to see if leaked prefixes have been installed:
!
A2#show ip route isis
Gateway of last resort is 10.0.0.25 to network 0.0.0.0
i*L1 0.0.0.0/0 [115/10] via 10.0.0.25, 04:15:38, GigabitEthernet0/1
192.168.0.0/32 is subnetted, 3 subnets
i L1 192.168.0.2 [115/20] via 10.0.0.25, 00:01:04, GigabitEthernet0/1
i ia 192.168.0.9 [115/50] via 10.0.0.25, 00:01:04, GigabitEthernet0/1
A2# show ipv6 route isis
IPv6 Routing Table - default - 7 entries
I1 ::/0 [115/10]
via FE80::F816:3EFF:FE39:9795, GigabitEthernet0/1
I1 2001:DB8:B:0:1::2/128 [115/20]
via FE80::F816:3EFF:FE39:9795, GigabitEthernet0/1
IA 2001:DB8:B:0:1::9/128 [115/50]
via FE80::F816:3EFF:FE39:9795, GigabitEthernet0/1
Both outputs verify that routes that have been identified to be redistributed from the L2 areas into the L1 area have been installed into routing tables of router A2.
Step8: On router B1, configure IPv4 prefix-list to match the IP address of router A2's loopback0 interface, then configure route-map to match this prefix-list:
!
B1(config)#ip prefix-list A2-loopback-ipv4 permit 192.168.0.10/32
!
B1(config)#route-map ROUTE_LEAK_IPV4 permit 10
B1(config-route-map)#match ip address prefix-list A2-loopback-ipv4
B1(config-route-map)# end
Step9: On router B1, configure IPv6 prefix-list to match the IPv6 address of router E2's loopback0 interface, then configure route-map to match this prefix-list:
!
B1(config)#ipv6 prefix-list E2-loopback-ipv6 permit 2001:db8:b:0:1::b/128
!
B1(config)#route-map ROUTE_LEAK_IPV6 permit 10
B1(config-route-map)#match ipv6 address prefix-list E2-loopback-ipv6
B1(config-route-map)#end
Step10: Redistribute both IPv4 and IPv6 prefixes identified in previous steps 8 and 9:
!
B1(config)#router isis
B1(config-router)#redistribute isis ip level-2 into level-1
route-map ROUTE_LEAK_IPV4
!
B1(config-router)#address-family ipv6
B1(config-router-af)#redistribute isis level-2 into level-1 route-map ROUTE_LEAK_IPV6
B1(config-router-af)#
Step11: Verify that the route leaking configuration was performed properly by checking the running-config on the router B1:
B1#show running-config | section router isisrouter isis
net 49.b000.0000.0000.00b1.00
redistribute isis ip level-2 into level-1 route-map ROUTE_LEAK_IPV4
!
address-family ipv6
redistribute isis level-2 into level-1 route-map ROUTE_LEAK_IPV6
exit-address-family
Step12. On the router, B2 verify that B1 propagates the IPv4 and IPv6 leaked routes by checking both the IS-IS database and routing table:
B2#show isis database detail B1.00-00
IS-IS Level-1 LSP B1.00-00
LSPID LSP Seq Num LSP Checksum LSP Holdtime/Rcvd ATT/P/OL
B1.00-00 0x0000001B 0xCC80 838/1199 1/0/0
Area Address: 49.b000
NLPID: 0xCC 0x8E
Hostname: B1
Metric: 10 IS B1.01
IP Address: 192.168.0.1
Metric: 10 IP 10.0.0.16 255.255.255.252
Metric: 10 IP 192.168.0.1 255.255.255.255
Metric: 50 IP-Interarea 192.168.0.10 255.255.255.255
IPv6 Address: 2001:DB8:B:0:1::4
Metric: 10 IPv6 2001:DB8:B:0:1::4/128
Metric: 10 IPv6 2001:DB8:A:0:1:1:0:10/126
Metric: 40 IPv6-Interarea 2001:DB8:B:0:1::B/128
The output confirms that both the IPv4 route of router A2 and IPv6 prefix of router E2 are in the IS-IS database of router B2.
B2#show ip route isis
Gateway of last resort is 10.0.0.17 to network 0.0.0.0
i*L1 0.0.0.0/0 [115/10] via 10.0.0.17, 04:48:12, GigabitEthernet0/1
192.168.0.0/32 is subnetted, 3 subnets
i L1 192.168.0.1 [115/20] via 10.0.0.17, 00:03:51, GigabitEthernet0/1
i ia 192.168.0.10 [115/60] via 10.0.0.17, 00:03:51, GigabitEthernet0/1
!
B2#show ipv6 route isis
IPv6 Routing Table - default - 7 entries
I1 ::/0 [115/10]
via FE80::F816:3EFF:FEFB:95F1, GigabitEthernet0/1
I1 2001:DB8:B:0:1::4/128 [115/20]
via FE80::F816:3EFF:FEFB:95F1, GigabitEthernet0/1
IA 2001:DB8:B:0:1::B/128 [115/50]
via FE80::F816:3EFF:FEFB:95F1, GigabitEthernet0/1
B2#
Finally, show commands for both IPv4 and IPv6 routing tables show that more specific routes to reach routers A2 and E2 have been installed.

Comments
Post a Comment